Azure Privileged Identity Management: Simple Power of using Groups
- Roman Guoussev-Donskoi
- Oct 17, 2021
- 2 min read
Context
Groups are one of the oldest techniques to scale identity management.
With the Azure PIM privileged access groups (preview), you can give workload-specific administrators quick access to multiple roles with a single just-in-time request. When the admins elevate into the group, they’ll become members of all Azure AD roles assigned to the group.
Additional details you can find on Microsoft documentation Management capabilities for Privileged Access groups (preview)
Summary
We found PIM privileged access groups capability very useful and added a layer to make it more flexible and believe better fit for larger enterprises. Specifically
Use Azure Activity Directory Groups to manage groups of users (reflect organization structure)
Use PIM Privileged access groups to group roles and privileges to be granted (functional roles)
Assign Azure AD Groups to PIM Privileged access groups as eligible members (instead of assigning individual users directly to PIM groups)
This allows us:
Delegate access reviews of organizational AD Groups to managers of specific departments
Clearly identify what departments require functional roles configured in PIM Privileged access groups
Still leverage PIM audit history of users activating PIM groups membership
Example
The setup if extremely simple as shown below
Create role-enabled Azure AD group to be used as PIM Privileged access groups

Grant required AD roles to group being created

You can check that the required roles have been added to the group

Enable PIM for the created group

The group will show now in PIM "Privileged access groups"

in Azure AD Groups blade create a new AAD group to represent the organizational department
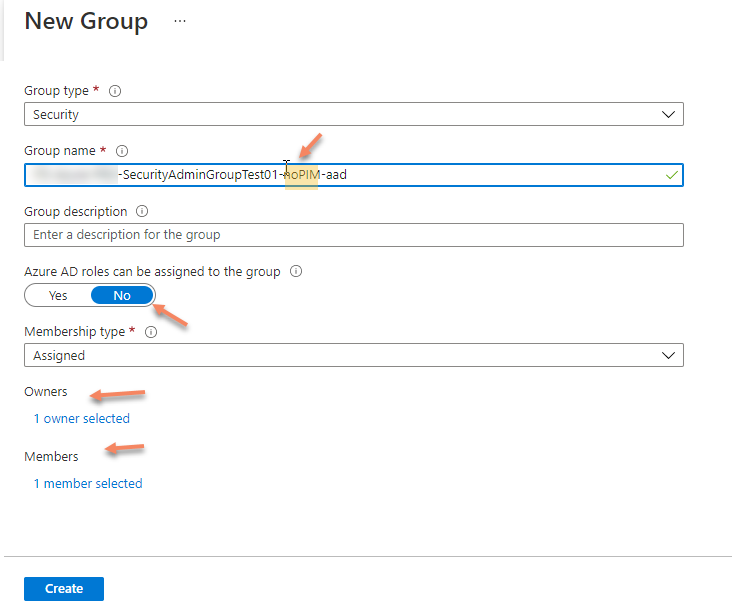
Now go to Privileged Identity Management and add assignment to previously created PIM group

Select the AAD group representing organizational unit as a member of PIM group

Click Next

Make member AAD group Eligible and specify maximum duration of this assignment

Now can see department AAD group in the list of Eligible assignments for PIM group. And no direct user assignments.

Users assigned as members of department AD group now can activate PIM group (even though no users directly assigned to PIM group)


Users can check in PIM that group has been activated

User can also check in PIM "My roles" that roles granted to PIM Group are assigned to them via group activation


User can click on "Group" link in Activated Role record shown above to see what group activated this role

PIM administrator can also still see in PIM group "Resource Audit" that user has activated PIM group


That is all.
Now we can have access reviews of group membership done by department group managers and the same time PIM administrator produce audit history of privileged access.
In our case this i exactly what was needed and this approach is easy to tune to to match specific organizational requirements.



Comentarios